iCACLS.exe (2003 sp2, Vista+)
Change file and folder permissions - display or modify Access Control Lists (ACLs) for files and folders.
iCACLS resolves various issues that occur when using the older CACLS & XCACLS.
Syntax
Add or remove permissions:
ICACLS Name
[/grant[:r] User:Permission[...]]
[/deny User:Permission[...]]
[/remove[:g|:d]] User[...]]
[/inheritance:e|d|r ]
[/setintegritylevel Level[...]]
[/T] [/C] [/L] [/Q]
Store ACLs for one or more directories matching name into aclfile for later use with /restore:
ICACLS name /save aclfile [/T] [/C] [/L] [/Q]
Restore ACLs to all files in directory:
ICACLS directory [/substitute SidOld SidNew [...]]
/restore aclfile [/C] [/L] [/Q]
Change Owner:
ICACLS name /setowner user [/T] [/C] [/L] [/Q]
Find items with an ACL that mentions a specific SID:
ICACLS name /findsid Sid [/T] [/C] [/L] [/Q]
Find files whose ACL is not in canonical form or with a length inconsistent with the ACE count:
ICACLS name /verify [/T] [/C] [/L] [/Q]
Replace ACL with default inherited acls for all matching files:
ICACLS name /reset [/T] [/C] [/L] [/Q]
This is equivalent to “Replace all child permission entries with inheritable permission from this object” in the GUI.
Key
name The File(s) or folder(s) the permissions will apply to.
/T Traverse all subfolders to match files/directories. This will apply permission changes to
all subfolders whether or not they are set to inherit permissions from the parent. On very large
directory structures this may take some time as the command has to traverse the entire tree.
/C Continue on file errors (access denied) Error messages are still displayed.
/L Perform the operation on a symbolic link itself, not its target.
/Q Quiet - supress success messages.
/grant :r user:permission
Grant access rights, with :r, the permissions
will replace any previouly granted explicit permissions (for the given user).
Otherwise the permissions are added.
/deny user:permission
Explicitly deny the specified user access rights.
This will also remove any explicit grant of the
same permissions to the same user.
/remove[:[g|d]] User
Remove all occurrences of User from the acl.
:g remove all granted rights to that User/Sid.
:d remove all denied rights to that User/Sid.
/inheritance:e|d|r
e - Enable inheritance
d - Disable inheritance and copy the ACEs
r - Remove all inherited ACEs
/setintegritylevel [(CI)(OI)]Level
Add an integrity ACE to all matching files.
level is one of L,M,H (Low Medium or High)
Mandatory Label\Low Mandatory Level = Low.
Mandatory Label\Medium Mandatory Level = Medium/Standard.
Mandatory Label\High Mandatory Level = Elevated.
If No mandatory label is displayed in the output, it is Medium by default.
A Directory Inheritance option for the integrity ACE can precede the level
and is applied only to directories:
user A user account, Group or a SID
/restore Apply the acls stored in ACLfile to the files in directory
permission is a permission mask and can be specified in one of two forms:
a sequence of simple rights:
D - Delete access
F - Full access (Edit_Permissions+Create+Delete+Read+Write)
N - No access
M - Modify access (Create+Delete+Read+Write)
RX - Read and eXecute access
R - Read-only access
W - Write-only access
a comma-separated list in parentheses of specific rights:
DE - Delete
RC - read control
WDAC - write DAC
WO - write owner
S - synchronize
AS - access system security
MA - maximum allowed
GR - generic read
GW - generic write
GE - generic execute
GA - generic all
RD - read data/list directory
WD - write data/add file
AD - append data/add subdirectory
REA - read extended attributes
WEA - write extended attributes
X - execute/traverse
DC - delete child
RA - read attributes
WA - write attributes
inheritance rights can precede either form and are applied
only to directories:
(OI) - object inherit
(CI) - container inherit
(IO) - inherit only
(NP) - don’t propagate inherit
(I) - Permission inherited from parent container
Unlike earlier command-line tools, iCACLS correctly preserves the canonical ordering of ACE entries:
- Explicit Deny
- Explicit Grant
- Inherited Deny
- Inherited Grant
Access Control Lists apply only to files stored on an NTFS formatted drive, each ACL determines which users (or groups of users) can read or edit the file. When a new file is created it normally inherits ACL’s from the folder where it was created.
An access control list (ACL) is a list of access control entries (ACE). When backing up or restoring an ACL with iCACLS, you must do so for an entire directory (using /save and /restore) even if you are only interested in the ACEs for a few individual files. In practice most permissions are set at the per-directory level.
Multiple /Grant /Deny /Remove clauses can be included in a single icacls command, on a large directory tree this has the advantage that the tree only has to be traversed once, rather than multiple times if you were to issue several consecutive icacls commands instead.
The ability to delete or rename a folder is decided by a combination of the Delete permissions on the folder in question, plus the Delete subfolders and files permission on the parent folder.
Modify vs Full control
- To edit a file you must have the "Modify/Change" ACL (or be the file’s owner)
- To use the iCACLS command to change the permissions of a file requires "FULL Control" (or be the file’s owner)
- File "Ownership" will always override all ACL’s - you always have Full Control over files that you create.
Inheritance
Inherited folder permissions are given as:
OI - Object inherit - This folder and files. (no inheritance to subfolders)
CI - Container inherit - This folder and subfolders.
IO - Inherit only - The ACE does not apply to the current file/directory
These can also be combined as follows:
(OI)(CI) This folder, subfolders, and files.
(OI)(CI)(IO) Subfolders and files only.
(CI)(IO) Subfolders only.
(OI) (IO) Files only.
So BUILTIN\Administrators:(OI)(CI)F means that both files and Subdirectories will inherit 'F' (Full control)
similarly (CI)R means Directories will inherit 'R' (Read folders only = List permission)
It is worth spending some time working out which permissions can be inherited and which need to be applied directly. On large/complex directory structures, minimising the number of ACLs can improve fileserver performance.
If inheritance is combined with /T (traverse subfolders) the change will apply to all folders, not just the top level.
for example:
icacls "C:\demo\example" /inheritance:e /T
Will traverse all subfolders below"C:\demo\example" and enable the inheritance for every one, this will replace any inheritance permissions that have been removed.
If no inheritance is specified, inheritance rules will not be changed but existing inherited permissions will be re-applied to existing objects in the specified location for the specified users/groups.
for example:
icacls "C:\demo\example" /grant administrators:(F) /T
This is similar to applying /reset to the child items of "C:\demo\example" but only resets the administrators group.
By default, an object will inherit permissions from its parent object, either at the time of creation or when it is copied or moved. The only exception to this rule occurs when you move an object to a different folder on the same volume. In this case, the original permissions are retained. In controlled environments this ensures that users cannot change file permissions by just moving items to a different folder. This behaviour can be disabled by setting a system-wide registry key, see Q310316.
Built-In Groups
A command which addresses a built-in group by name like ICACLS foldername /GRANT Everyone:F /T
will only work when the system language is English.
To make this language independent, use an asterisk followed by the well-known SID for the group, see Q243330 for a list.
For example, to grant full control to Everyone on a folder: ICACLS foldername /GRANT *S-1-1-0:F /T
Running icacls under PowerShell
The options for icacls do not run easily under PowerShell, because brackets ( ) have a special meaning in PowerShell, to pass a bracket symbol to an external program it must be escaped with a backtick.
Alternatively, use the stop-parsing symbol --%
e.g.
: icacls "C:\demo\" --% /grant:r Administrators:(OI)(CI)F /T
A more 'PowerShell' approach which gives improved readability for complex icacls commands, is to set a variable for each option and then execute icacls with Invoke-Expression which will expand all the variables:
# Set PS variables for each of the icacls options
$Path = "c:\demo" #The path must be the first thing passed to icacls
$Grant = "/grant:r"
$Remove = "/remove"
$replaceInherit = "/inheritance:r"
$permission = ":(OI)(CI)(F)"
$useraccount1 = "ss64dom\simon"
$useraccount2 = "administrators"
# Run icacls using invoke Expression
Invoke-Expression -Command ('icacls $Path $replaceInherit $Grant "${useraccount1}${permission }"')
Examples
Change the NTFS permissions on C:\demo\example\, remove all existing inherited permissions and replace with Full control for the Administrators group and Change/Modify permission for jsmith.
Apply the new permissions to the folder and inherit down to subfolders and files (OI)(CI):
icacls "C:\demo\example" /inheritance:r /grant:r Administrators:(OI)(CI)F
icacls "C:\demo\example" /grant:r Administrators:(OI)(CI)F /T
icacls "C:\demo\example" /grant:r ss64Dom\jsmith:(OI)(CI)M /T
or you can combine grants like:
icacls "C:\demo\example" /grant:r Administrators:(OI)(CI)F /T /grant:r ss64Dom\jsmith:(OI)(CI)M /T
View the permissions currently set on a folder:
icacls "C:\demo\example"
Grant the group FileAdmins 'Delete' and 'Write DAC' permissions to C:\demo\example:
icacls "C:\demo\example" /grant:r FileAdmins:(D,WDAC)
Reset permissions on all child items below C:\demo\example\, note the use of \*, without that, the permissions would be reset to those of C:\demo\
icacls "C:\demo\example\*" /c /t /reset
Propagate a new permission to all files and subfolders of C:\demo\example\, without using inheritance:
(so if any of the subfolders contain specific permissions, those won’t be overwritten)
icacls "C:\demo\example" /grant:r accountName:(NP)(RX) /T
Backup the ACLs of every file in the current directory:
icacls * /save Myacl_backup.txt
Restore ACLS using a previously saved acl file:
icacls /restore Myacl_backup.txt
Change the Integrity Level (IL) of a file to High:
icacls MyReport.doc /setintegritylevel H
Remove all inheritance on the 'Demo' folder and grant access to the domain user 'Volta', in this command the /t will traverse existing subfolders and files, and the (CI) will ensure that new folders/files added in future will inherit these permissions:
icacls C:\demo\example /inheritance:r /grant SS64dom\Volta:(CI)F /t
Grant the user jdoe rights to create, edit and delete files in the folder C:\demo\example\, but prevent deletion of the folder itself:
:: First remove inheritance and grant admins Full control to the top folder
icacls "C:\demo\example" /inheritance:r /grant:r administrators:(OI)(CI)(F)
:: Grant Modify + Delete Child to subfolders and files only
icacls "C:\demo\example" /grant:r ss64Dom\jdoe:(OI)(CI)(IO)(M,DC) /T
:: Grant Read/Execute, Write and Append to the top level folder
icacls "C:\demo\example" /grant:r ss64Dom\jdoe:(RX,WD,AD)
:: if any pre-existing subfolders Grant admins Full control
icacls "C:\demo\example" /grant:r administrators:(OI)(CI)(F) /T
The above does set the correct permissions, but an undesired bug/side effect is that within the top level folder the Windows Explorer right click option to create New files will be empty - only New Folder is shown:
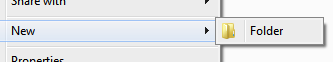
“It’s easier to ask forgiveness than it is to get permission” ~ Rear Admiral Grace Hopper
Related commands
ATTRIB - Display or change file attributes.
CACLS - Change file permissions.
DIR /Q - Display the owner for a list of files (try it for Program files).
FSUTIL - File System Options.
NTRIGHTS - Edit user account rights.
PERMS - Show permissions for a user.
TAKEOWN -
Take ownership of file(s).
XCACLS - Display or modify Access Control Lists (ACLs)
for files and folders.
SetObjectSecurity - Set security for an object (file, directory, reg key etc).
Syntax-Permissions - Explanation of permissions.
Q243330 - Well-known security identifiers (sids) in Windows operating systems.
Q220167 - Understanding Container Access Inheritance Flags.
Q310316 - Force Copy Acl with File.
AccessEnum - SysInternals GUI to browse a tree view of user permissions.
SetObjectSecurity.exe - Coming soon as part of the Security Compliance Toolkit.
PowerShell equivalent: Get-Acl / Set-Acl - Set permissions.
Equivalent bash command (Linux): chmod / chown - Change file permissions/owner and group.
Copyright © 1999-2024
SS64.com
Some rights reserved
